Appearance
Mastering Cloud Native DevSecOps: Top Security Practices for a Resilient Future ☁️🚀♾️📈
The cloud is vast, but fear not, fellow traveler! As organizations increasingly embrace cloud native architectures—leveraging microservices, containers, serverless functions, and dynamic orchestration—the traditional approaches to security are simply no longer sufficient. The very nature of cloud native, with its rapid deployments, distributed components, and ephemeral infrastructure, expands the attack surface and introduces new complexities.
This is where DevSecOps becomes not just a buzzword, but an absolute imperative. DevSecOps is about embedding security into every stage of the software development lifecycle, shifting security "left" to make it an integral part of development and operations, rather than a late-stage gate. For cloud native environments, this integration is critical for building resilient, secure, and compliant applications.
In this comprehensive guide, we will dive deep into the essential DevSecOps security best practices tailored specifically for cloud native applications. We'll explore strategies that empower teams to build security in from the ground up, automate safeguards, and maintain a proactive posture against evolving threats.
Why DevSecOps is Crucial for Cloud Native?
Cloud native development brings unparalleled speed and scalability, but also unique security challenges:
- Dynamic Environments: Resources are constantly provisioned, scaled, and de-provisioned.
- Distributed Systems: Microservices communicate over networks, increasing potential attack vectors.
- Containerization & Orchestration: Securing container images, registries, and Kubernetes clusters requires specialized approaches.
- Ephemeral Nature: Traditional perimeter-based security is less effective when components are short-lived.
- Shared Responsibility Model: Understanding and implementing your part of cloud security is paramount.
DevSecOps addresses these challenges by fostering a culture of shared security responsibility and automating security controls, enabling continuous assurance in highly dynamic environments.
Key DevSecOps Security Best Practices for Cloud Native
Let’s explore the fundamental practices that form the backbone of a strong cloud native DevSecOps strategy.
1. Shift-Left Security: Bake it in, Don't Bolt it On
The "shift-left" philosophy is at the core of DevSecOps, advocating for integrating security from the earliest stages of development.
Secure Coding Guidelines & Training: Educate developers on common vulnerabilities (OWASP Top 10) and secure coding patterns. Provide tools that offer immediate feedback within their IDEs.
Threat Modeling: Systematically identify potential threats and vulnerabilities early in the design phase. This proactive approach helps in designing security controls before code is even written.
Static Application Security Testing (SAST): Integrate SAST tools into your Continuous Integration (CI) pipeline to analyze source code for common security flaws without executing the code.
Example SAST integration in a CI pipeline (pseudo-YAML):
yaml# .github/workflows/sast-scan.yml name: SAST Scan on: [push, pull_request] jobs: sast: runs-on: ubuntu-latest steps: - uses: actions/checkout@v3 - name: Run SAST Scan # Replace with your actual SAST tool command run: | echo "Running SAST scan..." # Example: analyze code with a SAST tool # sast-tool scan --project-dir . --output-format sarif > sast-results.sarif echo "SAST scan completed."Software Composition Analysis (SCA): Automatically identify and manage open-source components, checking for known vulnerabilities and license compliance.
Dynamic Application Security Testing (DAST): Test running applications for vulnerabilities by simulating attacks. While often executed later, early DAST in pre-production environments can catch issues before deployment.
2. CI/CD Pipeline Integration: Automate, Automate, Automate!
The CI/CD pipeline is the perfect place to enforce and automate security checks, ensuring that only secure code reaches production.
Automated Security Testing: Embed SAST, SCA, DAST, and container image scanning directly into your build and deployment pipelines. Fail builds that don't meet defined security thresholds.
Vulnerability Scanning (Container Images): Scan container images for known vulnerabilities before they are pushed to registries or deployed. Use tools like Clair, Trivy, or integrated cloud provider services.
Policy as Code: Define security policies in code (e.g., OPA Gatekeeper for Kubernetes admission control, Sentinel for Terraform) and enforce them automatically throughout the pipeline. This ensures consistent application of rules.
Example of a simple policy check (pseudo-code):
regopackage kubernetes.admission deny[msg] { input.request.kind.kind == "Pod" # Deny pods that run with root privileges input.request.object.spec.securityContext.runAsNonRoot != true msg = "Pods must not run as root. Set securityContext.runAsNonRoot to true." }
3. Runtime Security and Observability: See Everything, Protect Always
Even with strong "shift-left" practices, continuous monitoring and runtime protection are crucial for identifying and responding to threats in live cloud native environments.
- Container and Kubernetes Runtime Protection: Implement solutions that monitor container behavior, detect anomalous activities, and enforce policies at runtime within your Kubernetes clusters.
- Logging, Monitoring, and Alerting: Centralize logs from all cloud native components (containers, hosts, services, cloud resources). Use monitoring tools to track security metrics and set up alerts for suspicious activities or policy violations.
- Incident Response (IR) Playbooks: Develop clear and actionable playbooks for responding to security incidents. Automate parts of the response where possible.
- Distributed Tracing: Gain deep visibility into microservice interactions to pinpoint the source and impact of security incidents.
4. Infrastructure as Code (IaC) Security: Secure Your Foundations
Infrastructure as Code (Terraform, CloudFormation, Pulumi) is fundamental to cloud native, but misconfigurations in IaC can lead to significant security vulnerabilities.
- IaC Scanning: Use tools (e.g., Checkov, Bridgecrew, Terrascan) to static-analyze your IaC templates for misconfigurations, compliance violations, and security risks before deployment.
- Immutable Infrastructure: Promote immutable infrastructure where once deployed, components are never modified. Any change requires a new, securely built deployment.
- Version Control for IaC: Treat IaC like application code, storing it in version control systems (Git) with proper review and approval processes.
5. Identity and Access Management (IAM): The Principle of Least Privilege
Robust IAM is non-negotiable for cloud native security.
- Least Privilege: Grant users and services only the minimum permissions necessary to perform their functions. Regularly review and revoke unnecessary access.
- Multi-Factor Authentication (MFA): Enforce MFA for all administrative and sensitive access.
- Strong Authentication: Use strong, unique credentials and integrate with identity providers.
- Secrets Management: Securely store and manage API keys, database credentials, and other sensitive information using dedicated secrets management solutions (e.g., HashiCorp Vault, AWS Secrets Manager, Kubernetes Secrets with encryption).
6. Supply Chain Security: Trust No One, Verify Everyone
In a cloud native world, applications often rely heavily on open-source libraries, third-party images, and external services, making supply chain security critical.
- Vetting Open-Source Components: Use SCA tools to continuously monitor and assess the security posture of open-source dependencies.
- Image Signing and Verification: Digitally sign your container images and verify signatures before deploying them to ensure their integrity and authenticity.
- Secure Registries: Use private, secure container registries (e.g., Docker Trusted Registry, AWS ECR, Azure Container Registry) and integrate them with vulnerability scanning.
Implementing DevSecOps for Cloud Native: A Practical Approach
Building a successful cloud native DevSecOps practice involves more than just tools; it requires a cultural shift and iterative refinement.
- Start Small, Iterate Often: Don't try to implement everything at once. Identify high-impact areas, automate one or two practices, and then expand.
- Cross-Functional Collaboration: Foster collaboration between development, security, and operations teams. Break down silos and ensure shared goals.
- Tooling: While tools are important, they are enablers, not solutions in themselves. Choose tools that integrate well with your existing ecosystem and support your workflows.
- Metrics and Feedback: Measure the effectiveness of your security controls. Use metrics (e.g., time to patch, number of vulnerabilities found, build failure rates due to security) to continuously improve.
Here's a visual representation of how security is interwoven into the cloud native CI/CD pipeline:
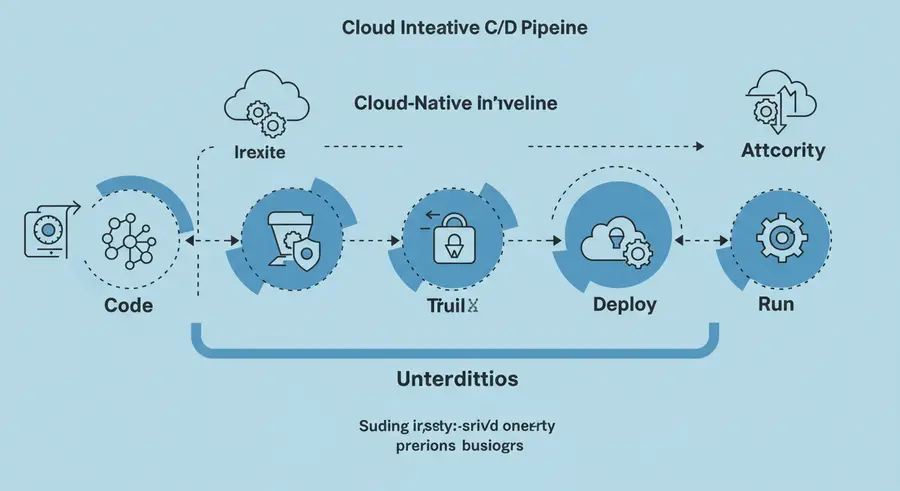
Conclusion
The journey to a truly secure cloud native environment is continuous. By embracing DevSecOps principles and implementing these best practices, organizations can build more resilient, trustworthy, and compliant applications. Remember, security is everyone's responsibility, and by automating and integrating it throughout your cloud native development lifecycle, you transform it from a barrier into an accelerant for innovation.
Let's architect for scale, code your infrastructure, and make observability key. Your cloud native castle awaits, fortified and ready!
References & Further Reading
- Cloud Native Application Security Best Practices: https://www.practical-devsecops.com/cloud-native-application-security-best-practices/
- 10 DevSecOps Best Practices to Implement Now: https://www.aquasec.com/cloud-native-academy/devsecops/10-devsecops-best-practices/
- Why DevSecOps is Key for Cloud Apps?: https://www.acldigital.com/blogs/best-practices-for-cloud-native-applications-using-devsecops
- Modern DevSecOps: Cloud-Native Security for Enterprise: https://tekleaders.com/modern-devsecops-cloud-native-security-strategies/
- Top 5 Cloud Security Best Practices for DevSecOps: https://www.crowdstrike.com/en-us/resources/white-papers/top-5-cloud-security-best-practices-devsecops/