Appearance
The cloud is vast, but fear not, fellow traveler! Today, we're charting a course through serverless landscapes, turning nebulous concepts into tangible, deployable solutions. Let’s automate our way to enlightenment.
Serverless architectures and robust CI/CD pipelines are a match made in cloud-native heaven. This powerful combination frees developers from the burdens of infrastructure management, allowing them to focus entirely on writing great code. Meanwhile, CI/CD automates the entire journey from code commit to deployment, ensuring your applications are delivered swiftly and reliably.
The Serverless Promise: Code, Not Servers
Serverless computing means you write your functions and deploy them, without needing to provision, scale, or manage any servers. It’s not that servers vanish; they just become someone else's problem! This shift dramatically accelerates development cycles, as you spend less time on operational overhead and more on innovation.
Think of AWS Lambda, API Gateway, and S3. With these services, you can build dynamic, scalable applications that respond to events, serve web content, and handle data processing—all without a single EC2 instance in sight.
CI/CD: Your Automation Superpower
Continuous Integration (CI) and Continuous Delivery/Deployment (CD) are the backbone of modern software development.
- Continuous Integration: Developers frequently merge their code changes into a central repository. Automated builds and tests then run to detect integration issues early.
- Continuous Delivery: Code is always in a deployable state, ready for manual release to production at any time.
- Continuous Deployment: The ultimate automation, where every change that passes all automated tests is automatically deployed to production.
When combined with serverless, CI/CD takes on a new level of efficiency. Imagine pushing a code change, and within minutes, your updated serverless function is live, handling user requests. This is the power we're talking about!
Building a Serverless CI/CD Pipeline: A Practical Walkthrough
Let's look at a typical serverless CI/CD pipeline, focusing on AWS and GitHub Actions.
Here's a simple, yet effective, architecture:
+------------------+ +------------------------+
| GitHub Repository|---->| GitHub Actions Pipeline|
| (Code & IaC) | +------------------------+
+------------------+ |
| (Triggers on Push)
v
+-----------------------------+
| GitHub Actions Workflow |
| |
| 1. Build & Test (Node.js/Python)|
| 2. Terraform Deploy Infrastructure |
| 3. Deploy Serverless Code (Lambda, S3) |
+-----------------------------+
|
v
+-----------------------------+
| AWS Cloud |
| +--------------+ |
| | API Gateway | |
| +------+-------+ |
| | |
| +------v-------+ |
| | AWS Lambda | |
| | (Functions) | |
| +--------------+ |
| |
| +--------------+ |
| | AWS S3 | |
| | (Static Site/ | |
| | File Storage)| |
| +--------------+ |
+-----------------------------+Here's how this pipeline works its magic:
- Code Commit: You push your application code (e.g., a Node.js Lambda function) and your Infrastructure as Code (IaC) — typically Terraform files — to your GitHub repository.
- GitHub Actions Trigger: A
pushevent to a specific branch (likemain) triggers a GitHub Actions workflow. - Build & Test: The workflow first runs your unit tests, linting, and any other quality checks on your application code. This ensures that only healthy code proceeds.
- Terraform Deploy Infrastructure: If tests pass, the pipeline then executes Terraform. Terraform reads your
.tffiles to provision or update your AWS resources:- API Gateway endpoints
- Lambda functions and their necessary permissions (IAM roles)
- S3 buckets for static website hosting or file storage
- Any other required services like DynamoDB tables or SQS queues. This step ensures your infrastructure is always in a desired, consistent state.
- Deploy Serverless Code: Once the infrastructure is ready, the pipeline packages your Lambda function code (e.g., a ZIP file) and uploads it to the newly created or updated Lambda function via the AWS CLI or an equivalent tool. If you have a static frontend, it might upload those files to your S3 bucket.
Code Your Infrastructure: Terraform in Action
IaC tools like Terraform are game-changers for serverless. They allow you to define your entire cloud infrastructure in declarative code, making it version-controlled, repeatable, and less prone to manual errors.
Here’s a simplified Terraform example for an AWS Lambda function and an API Gateway endpoint:
hcl
resource "aws_lambda_function" "my_function" {
function_name = "my-serverless-app-function"
handler = "index.handler"
runtime = "nodejs18.x"
role = aws_iam_role.lambda_exec_role.arn
filename = "lambda_function.zip" # This will be uploaded by the CI/CD
source_code_hash = filebase64sha256("lambda_function.zip") # For re-deployment on code change
}
resource "aws_api_gateway_rest_api" "my_api" {
name = "MyServerlessAPI"
description = "API for my serverless application"
}
resource "aws_api_gateway_resource" "proxy_resource" {
rest_api_id = aws_api_gateway_rest_api.my_api.id
parent_id = aws_api_gateway_rest_api.my_api.root_resource_id
path_part = "{proxy+}"
}
resource "aws_api_gateway_method" "proxy_method" {
rest_api_id = aws_api_gateway_rest_api.my_api.id
resource_id = aws_api_gateway_resource.proxy_resource.id
http_method = "ANY"
authorization = "NONE"
}
resource "aws_api_gateway_integration" "lambda_integration" {
rest_api_id = aws_api_gateway_rest_api.my_api.id
resource_id = aws_api_gateway_method.proxy_method.resource_id
http_method = aws_api_gateway_method.proxy_method.http_method
integration_http_method = "POST" # Lambda proxy integration typically uses POST
type = "AWS_PROXY"
uri = aws_lambda_function.my_function.invoke_arn
}
resource "aws_api_gateway_deployment" "api_deployment" {
rest_api_id = aws_api_gateway_rest_api.my_api.id
triggers = {
redeployment = sha1(jsonencode(aws_api_gateway_rest_api.my_api.body))
}
lifecycle {
create_before_destroy = true
}
}
resource "aws_api_gateway_stage" "production" {
deployment_id = aws_api_gateway_deployment.api_deployment.id
rest_api_id = aws_api_gateway_rest_api.my_api.id
stage_name = "production"
}
# Grant API Gateway permission to invoke the Lambda function
resource "aws_lambda_permission" "apigateway_lambda" {
statement_id = "AllowAPIGatewayInvokeLambda"
action = "lambda:InvokeFunction"
function_name = aws_lambda_function.my_function.function_name
principal = "apigateway.amazonaws.com"
source_arn = "${aws_api_gateway_rest_api.my_api.execution_arn}/*/*"
}This Terraform code sets up the necessary API Gateway and Lambda function. The lambda_function.zip artifact would be created and uploaded by your CI/CD pipeline in a separate step.
GitHub Actions Workflow Example
Here’s a snippet of a main.yml for your GitHub Actions workflow:
yaml
name: Serverless CI/CD
on:
push:
branches:
- main
jobs:
deploy:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v4
- name: Set up Node.js (or Python)
uses: actions/setup-node@v4 # or actions/setup-python@v5
with:
node-version: '18' # or '3.x' for python
- name: Install dependencies
run: npm install # or pip install
- name: Run tests
run: npm test # or python -m pytest
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v4
with:
aws-access-key-id: ${{ secrets.AWS_ACCESS_KEY_ID }}
aws-secret-access-key: ${{ secrets.AWS_SECRET_ACCESS_KEY }}
aws-region: us-east-1 # Your AWS region
- name: Install Terraform
uses: hashicorp/setup-terraform@v3
with:
terraform_version: 1.8.0 # Specify your desired Terraform version
- name: Terraform Init
run: terraform init
working-directory: ./infrastructure # Assuming your Terraform files are here
- name: Terraform Plan
run: terraform plan
working-directory: ./infrastructure
- name: Terraform Apply
run: terraform apply -auto-approve
working-directory: ./infrastructure
- name: Zip Lambda function code
run: zip -r lambda_function.zip . -x "*.git*" "node_modules/*"
working-directory: ./src/lambda-function # Path to your lambda code
- name: Deploy Lambda Function Code
run: aws lambda update-function-code --function-name my-serverless-app-function --zip-file fileb://lambda_function.zip
working-directory: ./src/lambda-function # Make sure the zip is accessibleThis workflow automates:
- Checking out your code.
- Setting up your language runtime and installing dependencies.
- Running your tests.
- Configuring AWS credentials using GitHub Secrets (highly recommended for security!).
- Initializing, planning, and applying your Terraform changes.
- Zipping your Lambda function code.
- Updating your Lambda function with the new code.
The Power of Synergy
This synergistic approach of serverless architectures and CI/CD pipelines offers immense benefits:
- Faster Release Cycles: Automate deployments means features get to users quicker.
- Reduced Operational Overhead: No servers to patch, scale, or worry about.
- Improved Reliability: Automated tests and IaC ensure consistency and reduce human error.
- Cost Efficiency: Pay only for what you use with serverless, and optimize resource allocation with IaC.
- Developer Focus: Developers can concentrate on business logic, not infrastructure.
The Visual Journey
Here's the visual representation of our serverless CI/CD journey:
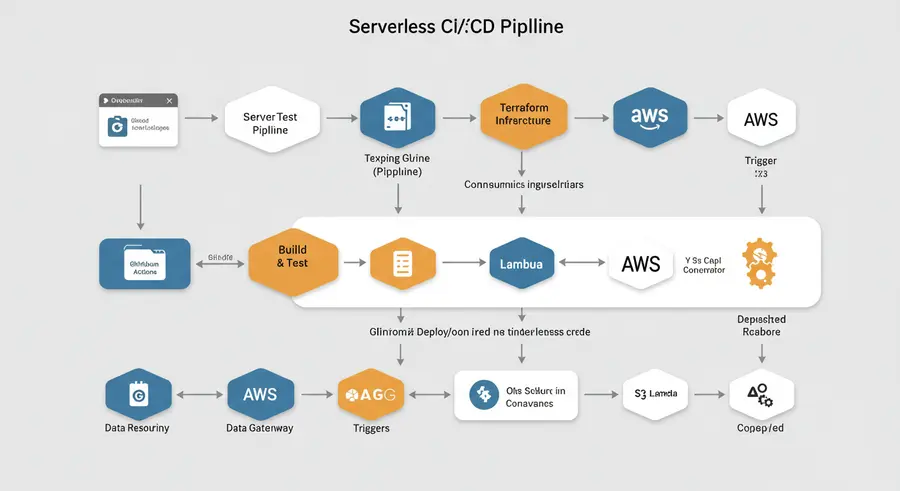
Let's Architect for Scale!
Embracing serverless and CI/CD is a transformative step for any team looking to build modern, agile, and resilient cloud-native applications. It’s about leveraging the cloud's full potential to deliver value faster and more reliably.
Remember, automate everything, resilience first, and simplify complexity. Happy deploying, fellow travelers! ☁️🚀♾️📈